Tag:cyber attack
Recent airport chaos revealed how fragile global infrastructure really is. A basic ransomware attack disrupted shared systems, grounding flights worldwide. The lesson is clear: outdated technology and rushed recovery leave industries exposed.

Airport Chaos Shows How Fragile Our Infrastructure Really Is
Recent airport chaos revealed how fragile global infrastructure really is. A basic ransomware attack disrupted shared systems, grounding flights worldwide.…

Anatomy of a Breach: Inside the Modern Retail Attack
Retail breaches don’t start with ransomware. They start with people. From social engineering to persistent access, attackers exploit the unseen…
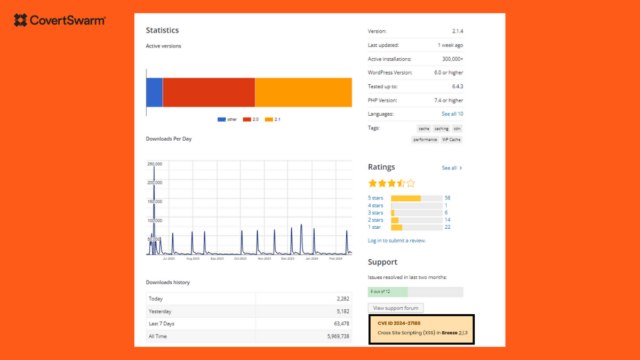
Discovering WordPress Vulnerabilities to Make it Safer
Breeze - WordPress Cache Plugin

Exploiting CVE-2023-5044 and CVE-2023-5043 to overtake a Kubernetes Cluster
In this blog we are exploring two new CVE's that exploit an issue in the NGINX controller when NGINX is…

Persistence Attack in Active Directory: The Golden Ticket Attack
Delve into the Golden Ticket Attack in Active Directory: a key APT method. Discover its workings, countermeasures, and detection to…

Our first Employee Net Promoter Score in review
CovertSwarm ranked as one of the leading industry employers after recording our first ‘excellent’ score

CovertSwarm named on the Startups 100 Index
Startup.co.uk has recognized us as one of the UK’s leading start-ups and part of the next generation of game changers.

What are insider threats and how do you prevent them?
Read our guide to understand what you need to know about insider threats, why they’re dangerous & how to identify,…

What’s the difference between red teaming and penetration testing?
Read our blog to find out the differences between red teaming & penetration testing & how to choose the right…