Threat actors don’t just want your data, they want your entire operation. Recent high-profile breaches have exposed a troubling reality: UK retailers face sophisticated adversaries who methodically map, breach, and exploit vulnerabilities across digital, physical, and human attack surfaces.
Modern retail breaches follow a predictable yet devastating pattern. Understanding this anatomy isn’t just academic, it’s essential for recognizing where your defenses may falter before real attackers exploit these gaps.
Groups like Scattered Spider have perfected social engineering tactics that bypass even robust technical controls by exploiting human psychology. Service desk staff, whose job is to help, become unwitting accomplices when faced with convincing pretexts.
A single well-crafted call can bypass MFA, reset credentials, and provide attackers with privileged access, all through legitimate channels that trigger no security alerts.
Under the radar
Once inside, attackers operate with calculated precision. They don’t immediately announce their presence with ransomware or data theft. Instead, they:
- Extract credentials from memory on compromised hosts
- Search internal file shares and collaboration platforms for sensitive documents
- Establish persistent access through legitimate remote access tools
- Deploy command and control infrastructure that mimics normal business traffic
This phase can last weeks or months as attackers map your environment, discover your crown jewels, and prepare for maximum impact.
Initial access: Scattered Spider used social engineering to bypass sophisticated controls, allowing them to move undetected once inside.
The path to compromise
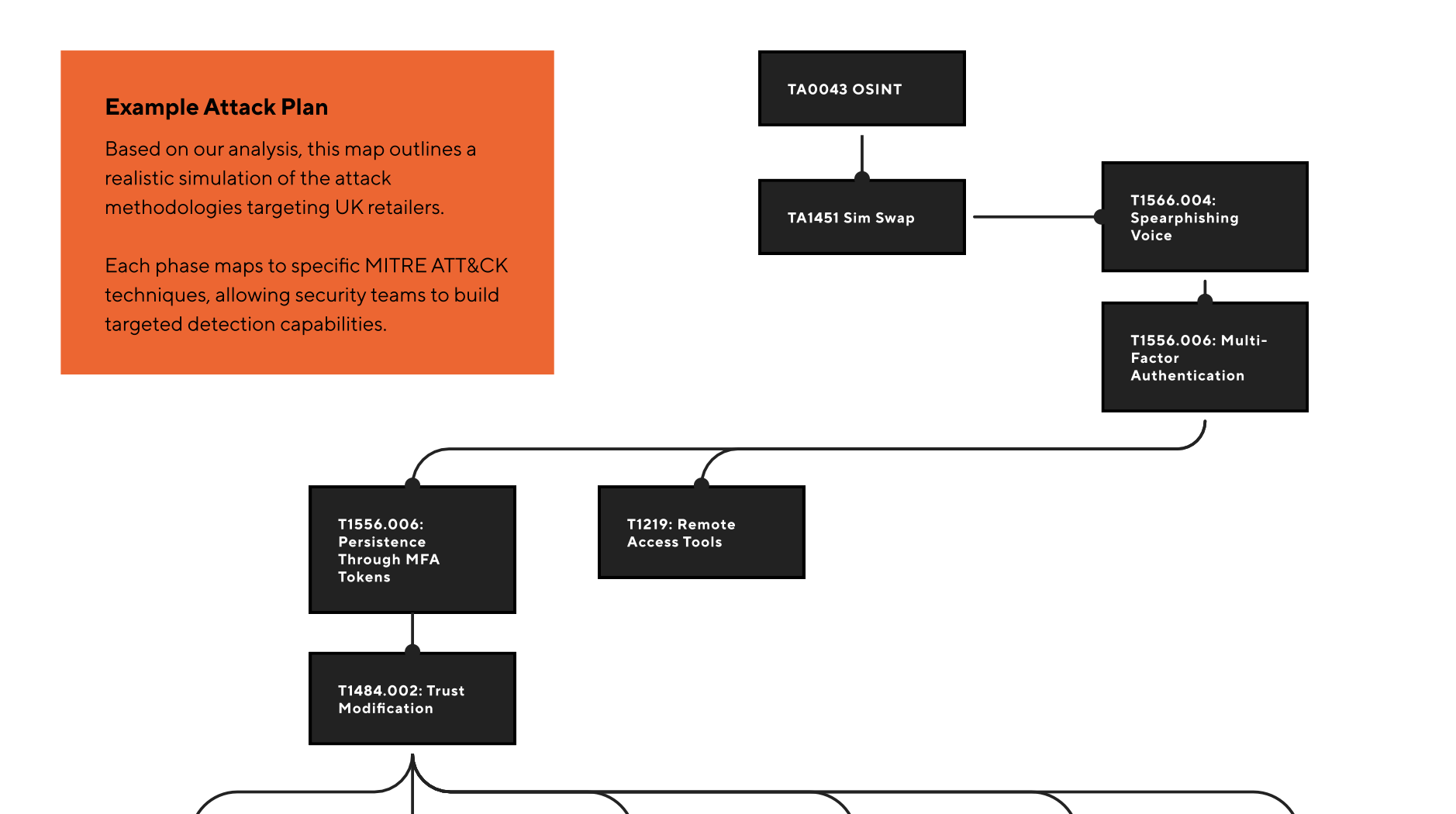
The initial access phase follows a sophisticated, multi-stage process that leverages both technical and human vulnerabilities. The attack typically begins with reconnaissance (TA0043 OSINT), where threat actors gather publicly available information about the target organization’s structure, employees, and technology stack.
Armed with this intelligence, attackers execute a SIM swap attack (TA1451) against key personnel. This technique involves convincing a mobile carrier to transfer a target’s phone number to an attacker-controlled device, effectively hijacking SMS messages and calls.
This crucial step enables the next phase: voice-based spearphishing (T1566.004).The spearphishing call typically targets the company’s service desk or IT support team. Using information gathered during the reconnaissance phase, the attacker impersonates a legitimate employee—often one with elevated privileges or a manager—and creates a convincing pretext for needing urgent access. Common scenarios include:
- Claiming to be working remotely and unable to access critical systems
- Pretending to be in a customer-facing situation requiring immediate access
- Presenting as an executive who needs urgent access before a critical meeting
When challenged with multi-factor authentication requirements (T1556.006), the attacker already has control of the target’s phone number through the earlier SIM swap, allowing them to intercept one-time passwords or approve push notifications. Once initial access is granted, the attackers establish persistence through compromised MFA tokens (T1556.006) and deploy legitimate remote access tools (T1219) that trigger minimal security alerts.
This approach allows them to establish a foothold without being detected by traditional security monitoring.
Download Inside the Spider
A full simulation of the Scattered Spider retail attacks. CovertSwarm’s elite team has reconstructed the TTPs used in recent high-profile breaches with tried and tested, realistic attack plans and purple team test scenarios.
Download
The devastating impact
When attackers finally reveal themselves, the damage is already extensive:
- Business operations come to a standstill
- Customer data is compromised
- Ransomware demands arrive
- Regulatory consequences loom
- Reputational damage spreads across news and social media
Are you ready?
The breach readiness checklist below addresses the critical gaps exploited in recent retail breaches:
- Have you tested your service desk against social engineering? Not through policy review, but through realistic simulation attacks.
- Do you have phishing-resistant MFA deployed? Push notifications aren’t enough. FIDO2 standards are rapidly becoming the minimum requirement.
- Are your identity systems hardened? Most modern retail breaches exploit weaknesses in identity architecture, not traditional network vulnerabilities.
- Do your detection capabilities cover legitimate tools used maliciously? Remote access tools, cloud platforms, and administrative utilities are all weaponized by modern attackers.
- Have you tested your incident response against realistic attack scenarios? Tabletop exercises based on outdated attack methods won’t prepare you for modern threats.
The gap between perception and reality
Most retailers believe their security investments have created adequate protection. Most are wrong.
The gap between perceived security and actual resilience represents the most significant business risk many organizations face today.
Sporadic testing for a limited time just won’t cut it when it comes to closing the cyber risk gap. Constant threat demands constant, targeted attack.
The consequences arising from this disparity can be severe, including financial loss and reputational damage.
Find your unknowns before attackers do
Today’s retail breaches aren’t the result of missing patches or overlooked vulnerabilities that appear on a scan report. They exploit the hidden gaps in your defenses, the blind spots in your security program that only surface during sustained and realistic attacks.
CovertSwarm’s offensive approach applies pressure to every part of your business, at every depth, to secure you through and through.
Our team constantly monitors your external attack surface, looking for changes and weaknesses that traditional security testing might miss.
Want to dive deeper?
Download our latest whitepaper for in-depth insights and practical recommendations.

