Attack Surface Management Portal
Outpace your cyber threats with the CovertSwarm Portal. How attack surface management portal should be.
Built for you by CovertSwarm.
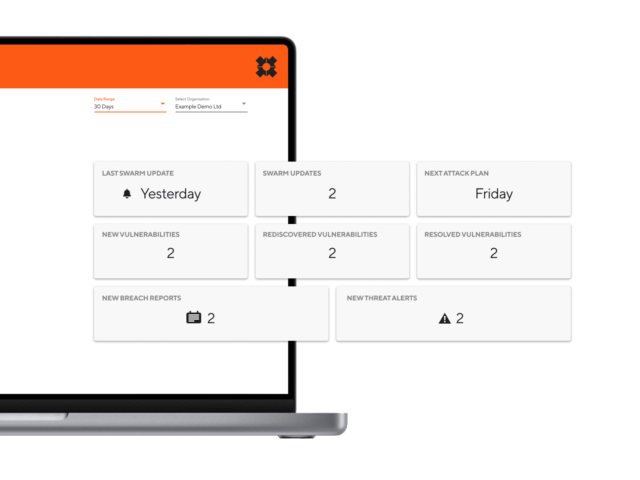
SUBSCRIBE TO CERTAINTY.
Finally, an attack surface management portal specifically built for the reality of modern cyber security.
Monitor threats and direct a dedicated Swarm of ethical hackers to any suspected weak areas of your business, in real time. Or let them roam free and compromise you just like a real attacker would. With CovertSwarm, you’re in control.
It’s what enables us to put the ‘constant’ into ‘Constant Cyber Attack’.
Overview of features
- Automated attack surface reconnaissance
- Attack surface change monitoring and alerting
- Dark web domain monitoring
- Breached credential discovery and alerting
- Asset discovery
- Direct integration with dedicated ethical hackers
- Slack and Jira integration
- Rolling 30 day contract with 10% annual discount offer
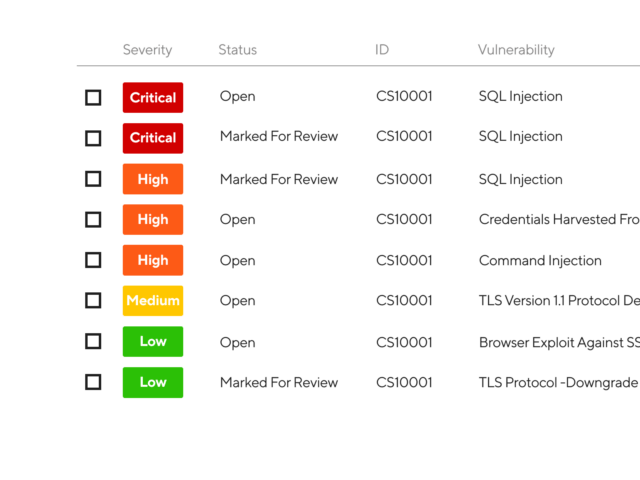
Shared intelligence
The CovertSwarm Portal captures detailed information about your business structure, processes, technology roadmap and architecture.
Focusing on people, process, technology and physical targets, it builds a holistic view of your potential risks to remove the cyber risk gap created by legacy attack surface management portal.
Get started today with a free account.

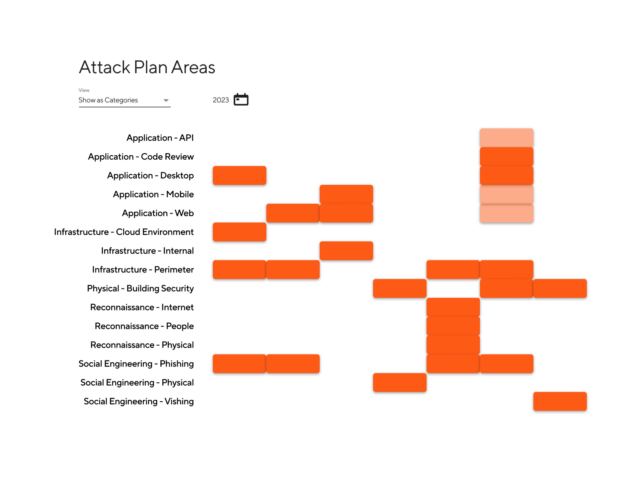
DIRECT THE SWARM.
From the CovertSwarm Portal interface, you can seamlessly direct our dedicated team of elite ethical hackers to attack any weak spot in your business, and simulate any attack.
It can be accessed from anywhere 24/7, giving you a complete picture of your constantly-evolving attack surface in real time. You’ll have total control to direct our research, continuous testing and attack procedures, with two-way communication between our attackers and your defense teams.
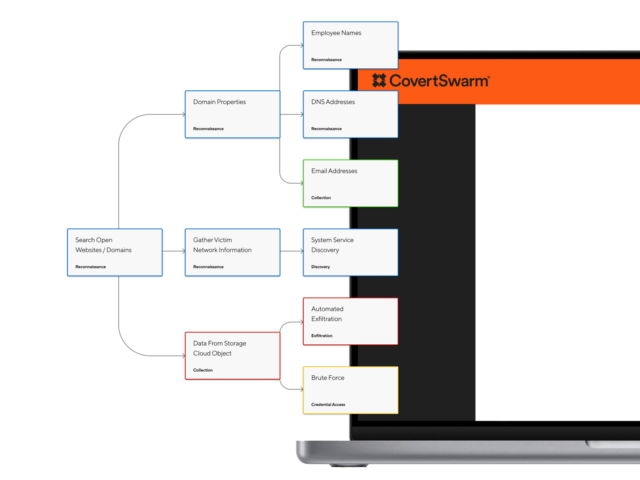
STOP TESTING. START ATTACKING.
Your approach to cyber attack must evolve to keep pace with organizational change. With most security breaches occurring many days prior to detection, effective simulated assaults must be constant.
With the CovertSwarm Portal, you’re only ever one click away from your best form of defence. Attack.
Subscribe to peace of mind.
Experience the only Attack Surface Management portal built by ethical hackers, specifically to meet the demands of constant offensive operations.
Attack surface management portal
Your organization is under attack. Several points of vulnerability have been compromised – some more vital than others. Better get your priorities in order, starting with an attack surface management plan.
What is attack surface management?
Attack surface management is a security strategy that continuously monitors, discovers, evaluates, prioritizes, and mitigates attack vectors in a company’s network. Everything from web applications and APIs to cloud infrastructure is monitored during this process. This never-ending assessment is designed to ensure all the latest threats are detected and eliminated before malicious actors get the chance to exploit them.
Our approach to attack surface management
As your company grows, your cyber attack surface expands and exposes you to a whole new range of threats. While other attack surface management companies may prefer a one-size-fits-all approach, we understand every organization is different and their needs should reflect this.
Our automated and continuous approach to external attack surface management is customisable to the priorities of each client. Our team of highly skilled security experts are CREST-accredited and trained to monitor activity to the highest standard.
Not only will you mitigate risks with the attack surface management portal, but you’ll also make informed decisions with complete and utter confidence. Our detailed reports and findings are designed to cut out the excess noise and sift through meaningless data, so you can enjoy truly impactful insights that deliver actionable results.
Close the cyber risk gap
Protect your reputation and your finances by closing the cyber risk gap before serious damage can be done. Monitor real-time threats with an attack surface management portal.
Be proactive, not reactive
Don’t wait for hackers to try to exploit your system for you to start taking your security defense seriously. Stay on the offensive and invest in attack surface management solutions.
Benefits of our attack surface management portal
Harness the power of continuous attack surface management and ensure every vulnerability is mitigated before malicious actors have the chance to exploit them.
- Meet compliance regulations and industry standards with ease
- Data breaches are costly; avoid legal penalties and meet industry regulations by accessing a detailed view of your attack surface.
- Use collective intelligence to make informed decisions and mitigate risks.
- Two minds are better than one, so imagine the strength a swarm of countless ethical hackers can exert with hundreds of years of collective experience under our belt.
Features of our attack surface management portal
Less noise, more focus
Reduce the noise created by a large volume of security alerts. Enjoy targeted insights into specific vulnerabilities. No more information overload. By cutting out the excess we provide greater focus.
Spend smart: save on security
Which cyber risk is the most imminent? Threats may be never-ending, but your budget isn’t. Allocate your resources to areas that need them the most and reduce the likelihood of even costlier security breaches.
Stay one step ahead at all times
Never stop improving your internal or external attack surface management. Strive for the highest level of security by encoding continuous monitoring and testing. With real-time alerts and monitoring, you can always stay one step ahead of malicious
Frequently Asked Questions
What is attack surface management and why is it important for cybersecurity?
Asset surface management aims to identify, monitor, evaluate, prioritize, and remediate your exposure to attacks. It does so continuously by considering your entire IT infrastructure. It uses the attacker’s perspective to detect and eradicate possible entry points that put your security stance in jeopardy.
Surface attack management is useful for companies of all industries and sizes because it helps identify rogue components that may be present in known and unknown assets. With the rise of cloud technologies, the prominence of remote working policies, and the growing use of personal devices at work, discovering and managing risks ahead of time is the essence.
How can I identify my organization’s attack surface?
An attack surface management portal will highlight all potential security risks and vulnerable entry points that your organization is exposed to. This encompasses known and potentially unknown assets within your system and network.
What are the common attack vectors and how can I protect against them?
Cybercriminals use a wide range of attack vectors to steal information and cause damage to your organization. Phishing, malware, social engineering, they’ll try anything they can to crack into your system. They can even use more than one vector at the same time.
To protect against attack vectors, you should aim to:
- Encrypt data on portable devices
- Install software updates regularly
- Implement a closed network
- Conduct regular audits and vulnerability tests
- Perform frequent penetration tests
- Install multi-factor authentication
- Enhance employee awareness and provide training workshops
- Invest in cyber asset attack surface management
How can I prioritize and manage my organization’s vulnerabilities?
Identifying potential threats is only the first step toward mitigating risk and resisting cyber-attacks. Once your cyber-attack surface management portal discovers the potential vulnerabilities, you’ll need to rank these threats in order of urgency. Analyze your security position and start to shut down the attempts in an efficient manner.
What are the benefits of using an attack surface management portal?
With a centralized attack surface management portal, you’ll have improved visibility to identify potential cybersecurity gaps. With a clear picture of your level of risk, comes a heightened understanding of how to manage and mitigate these potential threats.
Above all, these attack surface management tools help organizations reduce the likelihood of a security breach. Other benefits include streamlined security procedures, greater levels of compliance, enhanced threat intelligence, and significant cost savings.
How often should I conduct an attack surface assessment?
Continuous attack surface management is the best way to remain proactive rather than reactive. In a digital landscape, threats are constantly evolving so frequent monitoring is key.
Depending on the size and complexity of your organization’s IT infrastructure, you may have to conduct assessments more or less frequently. As a rule of thumb, it’s wise to roll out a new assessment every time your organization encounters major changes, like implementing new technology or updating software.
What are the key components of your attack surface management portal?
Several key components make up an enterprise attack surface management portal.
Firstly, the discovery phase takes place and a map of all your known and unknown assets is compiled. This asset inventory encompasses all assets within your network that must remain secure.
Then, a vulnerability scan is employed to identify possible weaknesses within your external and internal assets. If any areas of your company are exposed, threat intelligence will determine what they are, and risk assessments will determine the level of risk associated with your exposure.
Finally, remediation management helps you prioritize the order of vulnerabilities and provide insights on how to mediate the threats. You also receive a series of reports and metrics to help your organizations track their security progress.
How can I integrate your attack surface management portal with my overall security strategy?
To maximize your security posture and deter possible threats, you must integrate attack surface management tools into your overarching strategy. To ensure a seamless implementation process, you can create a customized integration plan that won’t disrupt current procedures. By incorporating a centralized portal into your external and internal attack surface management, you’ll gain a holistic perspective of your organization’s level of security.
Insights from the SWArm mind

Claude Jailbroken To Attack Mexican Government Agencies
A threat actor jailbroke Claude to orchestrate a month-long attack on Mexican government networks, stealing 150 GB of sensitive data. We analyze what really happened and…

Jayson E Street Joins CovertSwarm
The man who accidentally robbed the wrong bank in Beirut is now part of the Swarm. Jayson E Street joins as Swarm Fellow to help us…

iNTERCEPT – How A Small RF Experiment Turned Into A Community SIGINT Platform
I’ve always been fascinated by RF. There’s something about the fact that it’s invisible, the fact that you might be able to hear aircraft passing overhead…
Our services
Successful organizations are constant targets for malicious actors. Those who take security seriously don’t test their defenses once a year, they subscribe to CovertSwarm to attack continuously through our services.
- Breach and Attack Simulation Services
- Physical Cyber Attack Services
- Social Engineering Testing Services
- Red Team Services
- Penetration Testing Services
- Ethical Hacking Services
- Vulnerability Scanning
- Web Application Testing
- Ransomware Attack Simulation
- Phishing Attack Simulation
- Insider Threat Detection
- Password Strength Testing
- IT Infrastructure Testing