Resources
Radical thinking and constant research inform all we do. Think ahead with shared intelligence from our Swarm of ethical hackers.


What is social engineering in cybersecurity?
Discover the ins and outs of social engineering attacks and learn how to identify and prevent them with this comprehensive…

What is ethical hacking?
Read our guide about ethical hacking to find out what it is, why it’s important, its benefits and challenges and…

Red teaming: everything you need to know
Get the inside scoop on everything you need to know about red teaming. Find out why it's important for organizations…
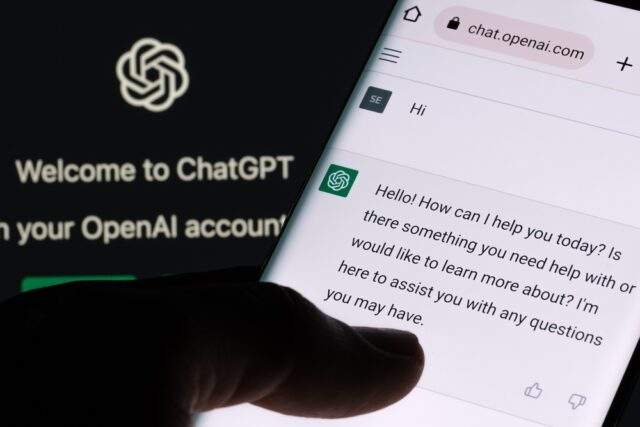
The risks, impact, and benefits of using AI generated content
In software development and security, AI can involve automating code generation, identifying vulnerabilities and detecting potential threats.

Security fatigue
It's not 'new news' that there have been numerous cybersecurity incidents across various industries over the last months, and whilst…

MFA Bombing
Why might your smartphone be pinging you in the middle of the night?

XSS – It’s not just “alert(1)”
XSS vulnerabilities can be an entry point that lead to wider issues. So you need someone to take them further…

Improving organisational awareness with enhanced Automated Reconnaissance
In the realm of cybersecurity, understanding the vulnerabilities in a system is crucial for any organisation to secure its digital…

Avoiding the Cyber Risk Rollercoaster
Over 100 global brands subscribe to CovertSwarm's Constant Cyber Attack service to out pace their genuine security threats.