Diary of a Cyber Attacker
When you think of an attacker, it’s tempting to imagine a Matrix-style hacker in a hoodie. In reality, these bad actors are highly intelligent experts in the cyber landscape — and they’re at the top of their game.
When you think of an attacker, it’s tempting to imagine a Matrix-style hacker in a hoodie. In reality, these bad actors are highly intelligent experts in the cyber landscape — and they’re at the top of their game.

Calling on an ever-expanding arsenal of stealthy exploitation frameworks and toolsets alongside personality traits like ruthlessness, creativity, curiosity and persistence, they’ll stop at nothing to extract, extort and destroy your information.
Protecting your people, customers and information is a constant battle, which is why an annual pen test just won’t cut it. Because while it might have you covered for one week of the year, what happens for the other 51? Using a fictitious example, let’s go inside the head of a hacker and find out…
This is interesting… MediaSec just announced their annual security audit. Let’s see how secure they really are. First, I’ll look at their organisation’s attack surface. I’ll need to figure out how their infrastructure works and any web applications they use. I can probably get most of this through a quick Google search…
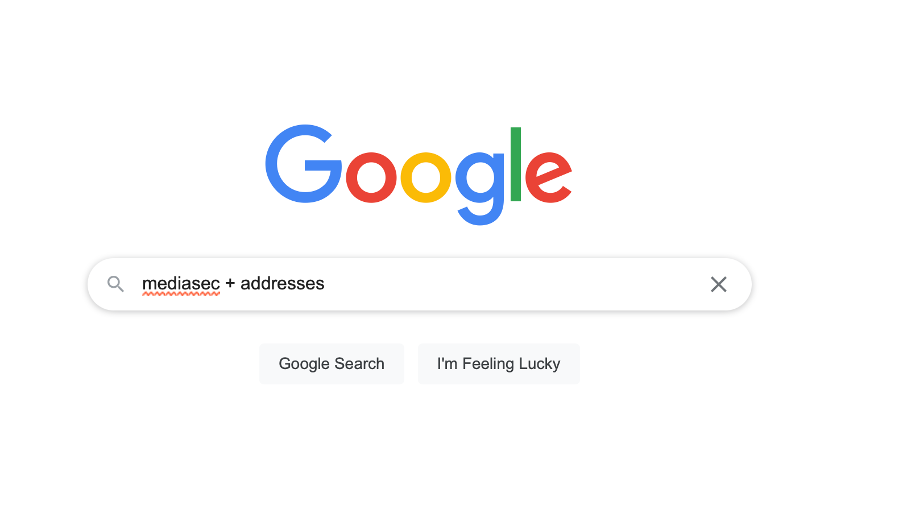
Great, this gives me links showing the autonomous system addresses, which gives me a helpful starting point for enumerating.

Next, I’ll use subdomain enumeration to find any other linked domains and IP addresses the target has.. Subfinder is pretty good, so I’ll start with that. And OWASP Amass was useful when I hacked that bank last time. Yep, there are a few bits and pieces here, so I’ll make a quick note.
Moving on, I’ll see if I can glean anything from MediaSec’s website… Hmm, there are few websites here in the footer that they own. And I could always take a quick look at MediaSec’s social media profiles too, in case they own any other companies. That’ll help to give me a bit more to go on with building a picture of their attack surface.
Boom, reams of domains and addresses I can target. I’ll get on that tomorrow.
Ah yes, there’s a huge list of address and domain names here. I’d better do a port scan next, to try and find addresses linked to useful services. But, I’ll need to be careful — if I don’t cover my tracks, this could be traced back to me.. I’ll use a VPN (virtual private network) to anonymise my activity and cover my tracks. I’ll use the same location as their company to avert suspicion.
Public sources such as Shodan and Censys haven’t told me much, so they may be blocking their originating address space… hmmm, tell you what – it’s a little more overt, but let’s see what NMAP will show me if I map their external network for commonly exposed services. It’ll help me look for potential ingress points to attack and compromise.
nmap -vvv --max-retries=1 --open -sV -Pn -r -p 21,22,23,80,443,1433,3306,3389,5900,5901 8080,-iL <iplist.txt> -oA <ports_output>
This could take a while. Best to leave it running overnight. I’ll come back to it in the morning.
The NMAP is finished, so I’ll take that output to make a shortlist of web applications. It’s easy to run some automation against those, to see if there’s anything of use. Looks like there are quite a few FTP services cropping up. If I try to identify the FTP server, I might find something I can leverage.
nmap -p21 -sV -A -iL ftp_list.txt -oX ftp_id.xml
Result. It’s come back with one instance of ProFTP that has a known weakness I can exploit. I’ll come back to that. And it’s also found some servers here with Microsoft Terminal Services exposed — that could give me remote control over a computer or virtual computer in their network. Better run some enumeration against these, too.
While all that’s going on, I’ll see what I can find from open source intelligence (OSINT) gathering. There’s bound to be tons of addresses and user information on social media, since people often use their work email to sign up to websites. Yep, just what I expected – a stash of email addresses, and I barely had to lift a finger. I could see if there are any more valuable ones using Google dorking — there’s a reason it’s the best search engine IMO. A few clever tricks and I’ll be able to get some of the more well-hidden stuff.
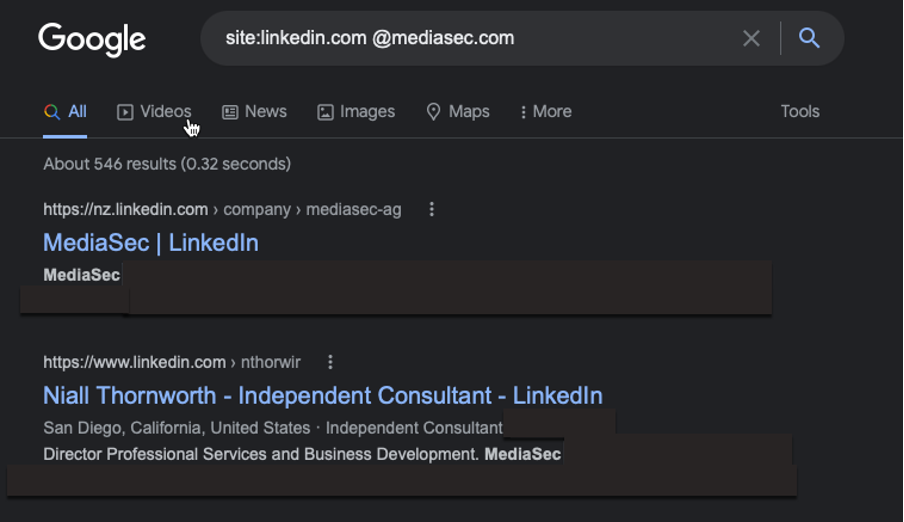
Great, I’ve got into their company LinkedIn. Oh look, office party pics — some snaps of the building layout there with computers on. And I’ve also got a good image of their ID badge format, too. I could use that information for social engineering. Now, let’s see about any company documents — I bet there will be some tidbits in here.

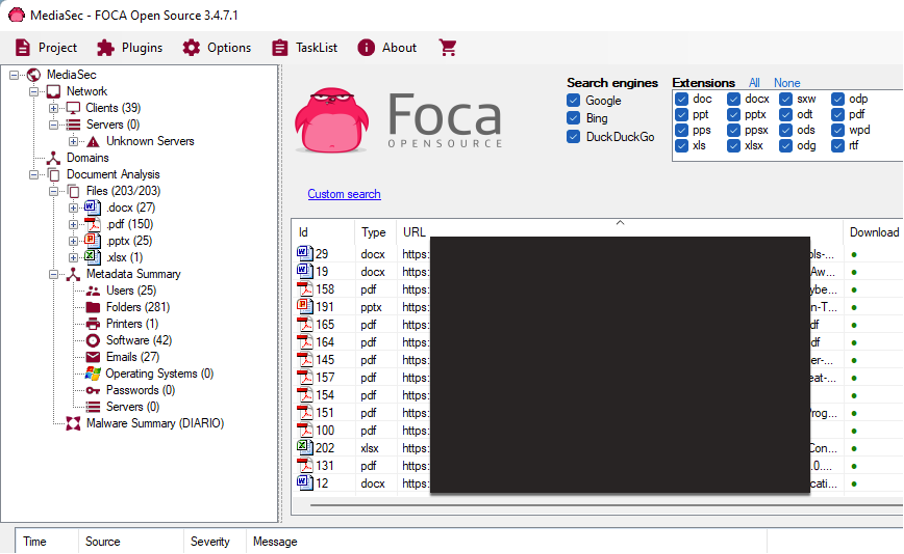
Okay, so there’s not much in the content from their publicly available documents, but I could try scanning the file metadata. FOCA is great for doing that. And… Success. I now have the internal domain name and username format, new email addresses, internal IP addresses and I can even work out what printers they use. Even better, there’s geo location data here showing where some of these images were taken, so I can find out if there are any more offices to target.
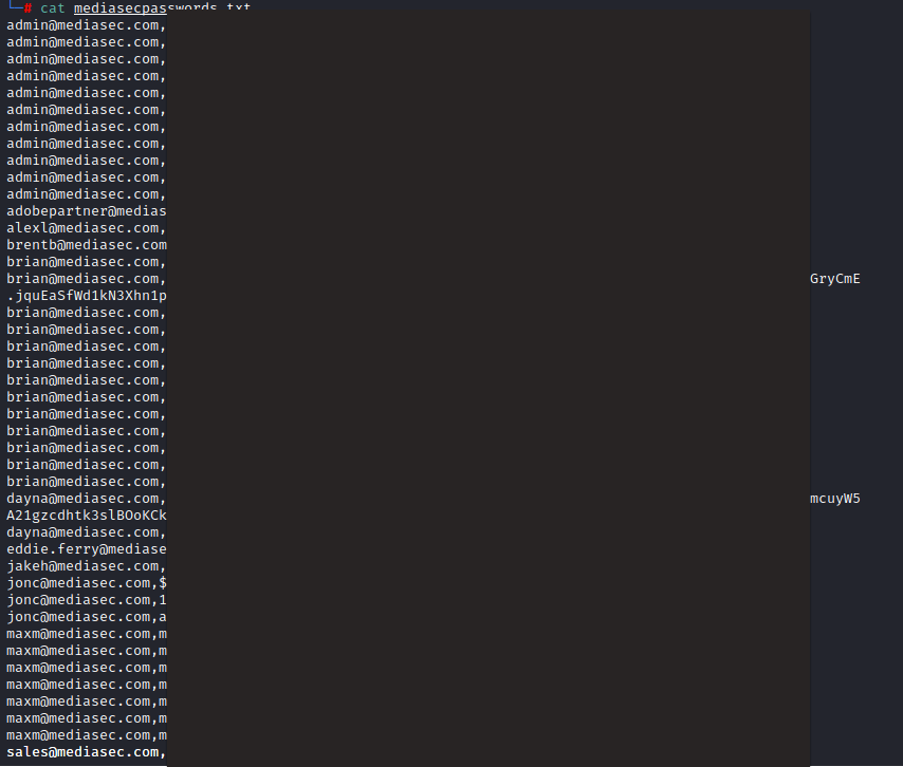
I wonder if there have been any recent data breaches for MediaSec? I’m sure I saw something in the press. I’ll hunt through the public data dumps I’ve amassed to find email addresses, and check if there are any shared breach data sources on the dark web too. If I find any email addresses with passwords, and they haven’t been changed since the breach, I’ll have an easy way in. But, even if I just get a few email addresses, it’s better than nothing — they’ll be ideal for brute force testing and phishing attempts.
With the emails I’ve found and a bunch of subdomains, I will test to see if they’re using Microsoft 365, which should be easy enough to find through Autodiscover records.
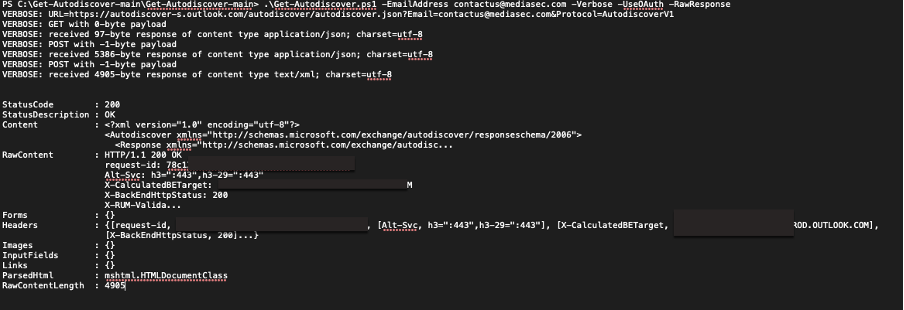
Great — they definitely use this for their email. I’ll try each email address to see which ones are still valid — I’ll be able to tell just based on the response I get from the portal when I enter the details. I might even be able to find out whether MFA (multi-factor authentication) is used on each account.
https://login.microsoftonline.com + email address
I can start this manually to assess any protections in place, then use some automation for the bulk. I’ll start going through it all properly tomorrow.
I’ve finished working through those now, and I’ve found a couple of addresses which don’t have MFA. FWIW, I can probably get into these using brute force to try simple passwords…
Nope, this isn’t working – Microsoft’s servers lock you out after three incorrect attempts, and I don’t want to alert their SOC or blue team to what I’m doing. I could try using a cloud approach, like Amazon Web Services, and change my IP after every few attempts. I’d better try this one password at a time, across all the accounts I’ve uncovered. I’ll try this one or two times, then take an hour’s break so that the attempt threshold resets and I don’t get locked out. This should give me better results and stop me getting detected.
Well, this is disappointing — no hits so far. I’ll Google a few more common passwords and give those a go. I know key dates, locations and sports teams names are popular choices. If I still can’t get in this way, I’ll try phishing the passwords directly using a man in the middle attack. I’ll just make a quick to-do list.
All done. Once they’ve clicked my link, I’ll lead them via my phishing workflow, which replicates the real Microsoft 365 portal sign-in. Fingers crossed for some credentials. If they have two-factor authentication, I’ll just account for that in the workflow and relay to the real Microsoft 365 portal in real-time.
I’m going to start splitting the users I’ve gathered into smaller groups for my fake emails. This will help get round monitoring triggers, which might pick up on a large email influx in one go from a single source. And, if my attack is picked up, I can switch attack vector with a different email approach.
I’ll now monitor the open rate, click rate and any credentials I’ve captured. This is a large company, so it’ll take time, and I’ll need to send the emails slowly and check back now and then. I’ll take another look later today…
Great, I’ve got a whole load of credentials to try. I’ll start trying them on the Microsoft Office 365 portal. They don’t use an office network or virtual private network to log in, so I can get into this from pretty much anywhere. Once I’m in, I can access the employee’s personal emails and even send an email to people in the company from their account — which I could use for more phishing attempts if I need to. I’ll also be able to get into all the Microsoft 365 applications like OneDrive, SharePoint, Teams and their cloud sharing.
User 1: [email protected]
Without MFA, I’ve got into this email account right away, but they can’t be very high up at MediaSec because they’ve only got limited access to the applications I need. Hang on — I’ve just seen an email in their inbox about the main company portal. I’ll try inputting the same password I used for their email address to get in… Yep, they’ve used the same credentials. Although… this time, there *is* MFA. Rookie mistake, though, because it’s just pinged an email straight into their inbox. I’ll just click the link to continue… And get access to the company portal, chat, and a database of users — plenty of useful stuff. I’ll park this user and come back later.
User 2: [email protected]
This should be a bit trickier because there’s MFA needed, but I’ve already accounted for this. When they entered their MFA token, their session cookie was captured and I can use it to grant access and jump in for a short period. I’ll need to be quick and get the bits I need before the cookie session expires… Lucky for me, this user has higher access and I can get into their personal OneDrive and SharePoint. I can even see a text file containing passwords in there… And, because I can get into their Microsoft 365 Admin portal, I can potentially download the entire company email address list, which will be handy for more phishing attacks.

Wait a second — an email has just popped up from the IT department about a potentially malicious email. Looks like they’re on to me. I need to download as much as I can as fast as possible, and get any more credentials for phishing. This has thrown a spanner in the works, though — if the IT guys know my email’s fake, they’ll know the address and domain it’s sent from is fake, too. No worries — I’ll start analysing the information I’ve got so far and make a plan for tomorrow.
It’s first thing in the morning — I doubt anyone at MediaSec is working right now. I’ve got some new credentials to try, and even though they’ve spotted my fake email, nobody knows I’ve hacked into those two accounts. I might have aroused suspicion slightly, but there’s no way the IT department will have asked anyone to change their passwords yet.
So, time to formulate my next steps…
With seven days of hacking attempts, you’d think the attacker would already have been foiled. Instead, they’re working hard to exploit the information they’ve gathered so far. Your company might be 9-5, but a bad actor works day and night — whatever suits their tactics — to find and crack your weaknesses. If you don’t protect your systems or educate your employees on cyber security, it won’t take long for a cyber criminal to find a back door. And when they do? The damage will be done, and you – and your customers – will be the last to know.
At CovertSwarm, we’ve got one thing malicious hackers don’t have: ethics. We use our knowledge, expertise and insights to protect every company by being the first to break in, whether you’re a mega enterprise like our fictional MediaSec, or a start-up SME with no IT department. That’s why we’re your modern, offensive security partner — we’ve done it for over 70 global brands, and we’re ready to do it for yours.

Claude Jailbroken To Attack Mexican Government Agencies
A threat actor jailbroke Claude to orchestrate a month-long attack on Mexican government networks, stealing 150 GB of sensitive data. We analyze what really happened and…

Jayson E Street Joins CovertSwarm
The man who accidentally robbed the wrong bank in Beirut is now part of the Swarm. Jayson E Street joins as Swarm Fellow to help us…

iNTERCEPT – How A Small RF Experiment Turned Into A Community SIGINT Platform
I’ve always been fascinated by RF. There’s something about the fact that it’s invisible, the fact that you might be able to hear aircraft passing overhead…