Tag:cybersecurity
Ellie joins to continue developing the industry-leading culture CovertSwarm is being recognized for.

Ellie Lancaster joins as Head of People and Culture
Ellie joins to continue developing the industry-leading culture CovertSwarm is being recognized for.

Rishikesh Bhide joins CovertSwarm as Head of Engineering
Rishikesh joins CovertSwarm to accelerate the organization’s engineering capabilities and product strategy as part of its rapid growth trajectory.

Louis Blackburn joins as Operations Director
Louis joins CovertSwarm from Lloyds Banking Group with an extensive background in red teaming, becoming the latest senior hire as…
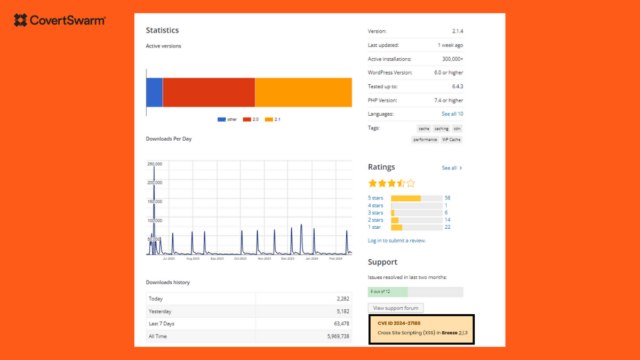
Discovering WordPress Vulnerabilities to Make it Safer
Breeze - WordPress Cache Plugin

Persistence Attack in Active Directory: The Golden Ticket Attack
Delve into the Golden Ticket Attack in Active Directory: a key APT method. Discover its workings, countermeasures, and detection to…

Our first Employee Net Promoter Score in review
CovertSwarm ranked as one of the leading industry employers after recording our first ‘excellent’ score

CovertSwarm named on the Startups 100 Index
Startup.co.uk has recognized us as one of the UK’s leading start-ups and part of the next generation of game changers.

CovertSwarm strengthens leadership team with three key senior appointments
We're preparing for another year of growth in 2024

We’ve been named a CISO Choice Awards finalist
The program recognized CovertSwarm as one of the world’s leading cybersecurity solutions