Improving organisational awareness with enhanced Automated Reconnaissance
In the realm of cybersecurity, understanding the vulnerabilities in a system is crucial for any organisation to secure its digital and physical assets.
In the realm of cybersecurity, understanding the vulnerabilities in a system is crucial for any organisation to secure its digital and physical assets.

CovertSwarm’s Offensive Operations Centre is a powerful platform that has been aiding organisations in gaining an understanding of their possible attack surface and where potential areas of risk are. Coupled with our dedicated professional services team, we’ve strived to provide a more complete picture of your organisation’s security health.
Using the information from the Offensive Operations Centre, organisations can prioritise their security efforts and develop a comprehensive security plan to mitigate risks. This may involve patching known vulnerabilities, updating software versions, and implementing additional security measures like firewalls, intrusion detection systems, and greater security awareness training. Additionally, we include the ‘soft’ side of an organisation’s assets such as the physical locations, processes, and the people that work within the organisation itself.
One of the ways that the Offensive Operations Centre does this is through leveraging custom-built automated reconnaissance tools. These are non-invasive processes that replicate what our professional services delivery team perform on a daily basis and pose no direct threat to the targeted assets. The goal of using these automations within the Offensive Operations Centre is to identify all possible entry points that a hacker could use to gain unauthorised access to an organisation and provide you with the same information that we would use during a targeted attack.
There are two methods of running the automated reconnaissance tools within the Offensive Operations Centre:
The relevant automations can be run individually or all at once
One being the point-and-click approach, by targeting individual assets directly. This allows for a more fine-grained approach if/when needed.
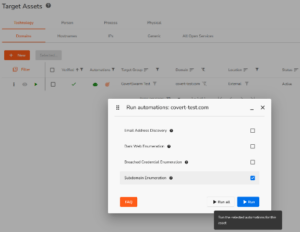
The relevant automations can be run individually or all at once
We’ve improved the user experience for how these can be triggered by making the run-button directly accessible from each respective asset, whilst also providing more visibility to each of the assets that are supported by the automation framework.
A quick glance can show the active or inactive scheduled reconnaissance jobs. The updated scheduling dialog now includes all of our automations
The second method is through our newly-extended scheduling system. Previously this only supported our port-scanning automation, which was widely well received from our existing customers.
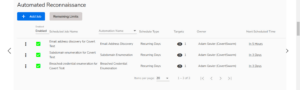
A quick glance can show the active or inactive scheduled reconnaissance jobs
However, this wasn’t good enough for us here at CovertSwarm – we want to empower people to have the same awareness, knowledge, and ability as our team.
We’ve extended the automated reconnaissance scheduler framework to include our full array of automations, and this will continue to be updated with each automation we implement in the coming weeks, months, and years.
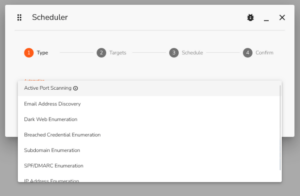
The updated scheduling dialog now includes all of our automations
Breaking down our automations that we have today, the ability to quickly discover assets is crucial to knowing “what is out there”; we provide the means to do this initially through domain based enumeration.
Our subdomain enumeration passively checks through publicly historised records for each domain alongside certificate transparency logs and additional sources. The aim of this is to provide a completely passive view (we are CovertSwarm after all) as to what an attacker could enumerate, but with the results of this including services and ports, software that is identified on each host/service, additional metadata such as where the server(s) are hosted, resolved IP addresses… and the list goes on.
The other ‘technology’ based enumerations focus upon delving deeper into infrastructure and applications. One of these being the IP enumeration, where we can further passively identify software, services, and so forth.
For those with a more direct approach mindset, we of course still provide our port scanning toolset, which allows for either quick discovery (such as a ping-sweep) or a more in-depth discovery that also returns a wealth of metadata (such as software) in addition to the expected services, ports, and protocols.
Two valuable automations, which I would personally recommended running semi-regularly, would be the Breached Credential and Dark Web enumerations:
Ultimately, awareness is the first step in understanding and structuring a perception of risk. The automations we have in place today are that initial stepping stone.
The future of the Offensive Operations Centre very much includes a greater amount of depth to our existing automations, providing more and better data to help support you and your organisation’s understanding of the security landscape, but also our professional services teams to drive further discovery and efficiencies during the delivery phases.
Additionally, recognising and alerting upon changes to your organisation’s attack surface is key. This is one critical area of importance for us, as a core part of CovertSwarm’s approach has always been to “cut through the noise”.
We welcome feedback from every customer we work with to feed in to the continued evolution of the platform. Our product development team are working hard alongside our expert professional services teams to continue building these great additions to the Offensive Operations Centre.
Stay tuned for more updates over the coming months.
If you would like to enquire about the Offensive Operations Centre please reach out to us via our contact form and our team will get back to you as soon as possible.

Claude Jailbroken To Attack Mexican Government Agencies
A threat actor jailbroke Claude to orchestrate a month-long attack on Mexican government networks, stealing 150 GB of sensitive data. We analyze what really happened and…

Jayson E Street Joins CovertSwarm
The man who accidentally robbed the wrong bank in Beirut is now part of the Swarm. Jayson E Street joins as Swarm Fellow to help us…

iNTERCEPT – How A Small RF Experiment Turned Into A Community SIGINT Platform
I’ve always been fascinated by RF. There’s something about the fact that it’s invisible, the fact that you might be able to hear aircraft passing overhead…