CovertSwarm: How our technology helps you
At CovertSwarm our mission is to constantly compromise our clients.
At CovertSwarm our mission is to constantly compromise our clients.
At CovertSwarm our mission is to constantly compromise our clients. That might sound a little odd to some, but the intention is pure; If we can work with you to identify where the weaknesses are within your organisation before the ‘bad actors’ are able to, then the net impact is that as a whole your security posture continues to improve.
One of the ways that we achieve this is by integrating our professional services delivery within your existing workflows (annual penetration testing, monthly releases, etc.) as an extension of your team. Still fully independent but trusted.
An issue with the traditional penetration testing approach can be the ramp-up time for an engagement, where the standard ‘Reconnaissance > Enumeration > Vulnerability Discovery > Exploitation > Reporting’ stages require those first two steps each and every time. This, coupled with the fact that organisations will often be assigned different personnel during the delivery phase of an engagement, can result in:
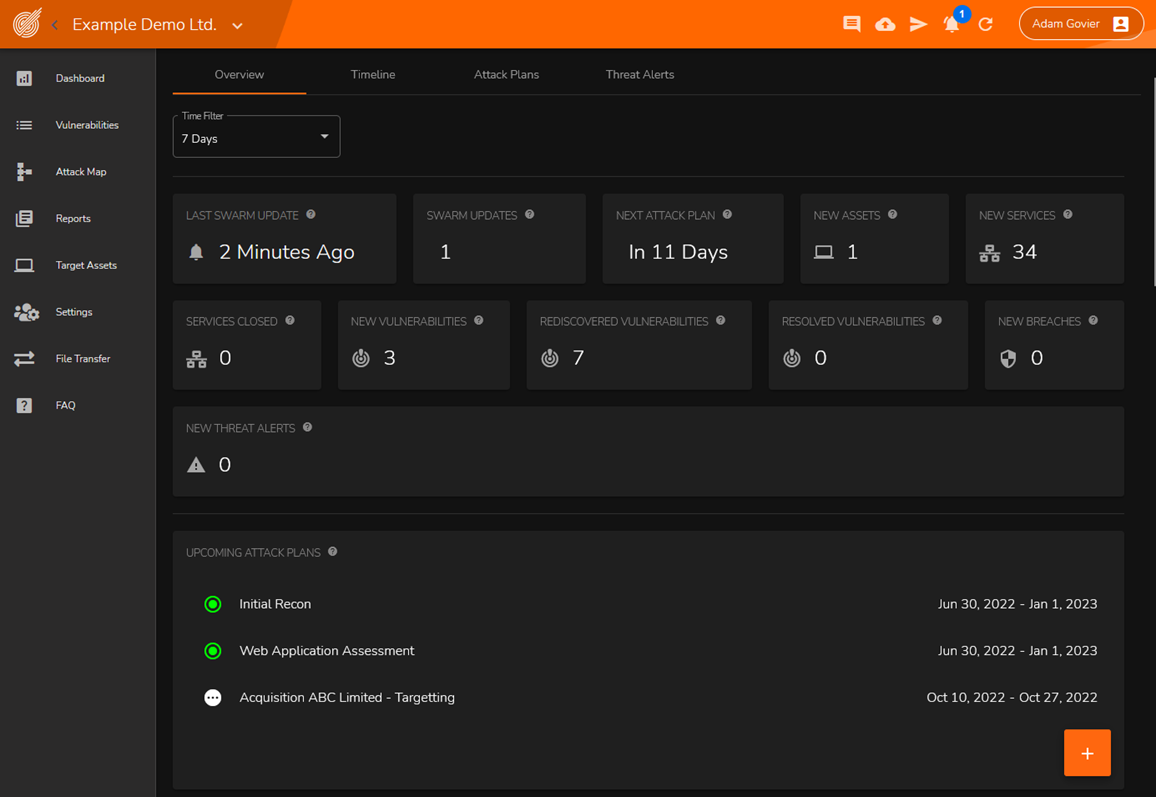
At CovertSwarm we provide all of our clients with access to the Offensive Operations Centre (our play on the Security Operations Centre).
If you’re already set up with the Offensive Operations Centre click here to access the portal.
The main goal of the Offensive Operations Centre (OOC for short) is to be a centralised interface for both your organisation and our professional services team. Here, every single asset, service, associated piece of software, vulnerability, report, and much more can be accessed to allow full visibility and control over the results of one or all offensive engagement cycles.
Having come from a background of penetration testing and red-teaming one of the main annoyances I’ve personally experienced with writing security/penetration testing reports in the days of old was having to associate an ‘asset’ as something technical, whether this be an IP address or a hostname/FDQN. This just doesn’t work for us here at CovertSwarm as our target is the organisation as a whole and everything related to them, not just the technology used by the business.
So, what’ve done is that we’ve broken down ‘Target Assets’ in to four main categories:
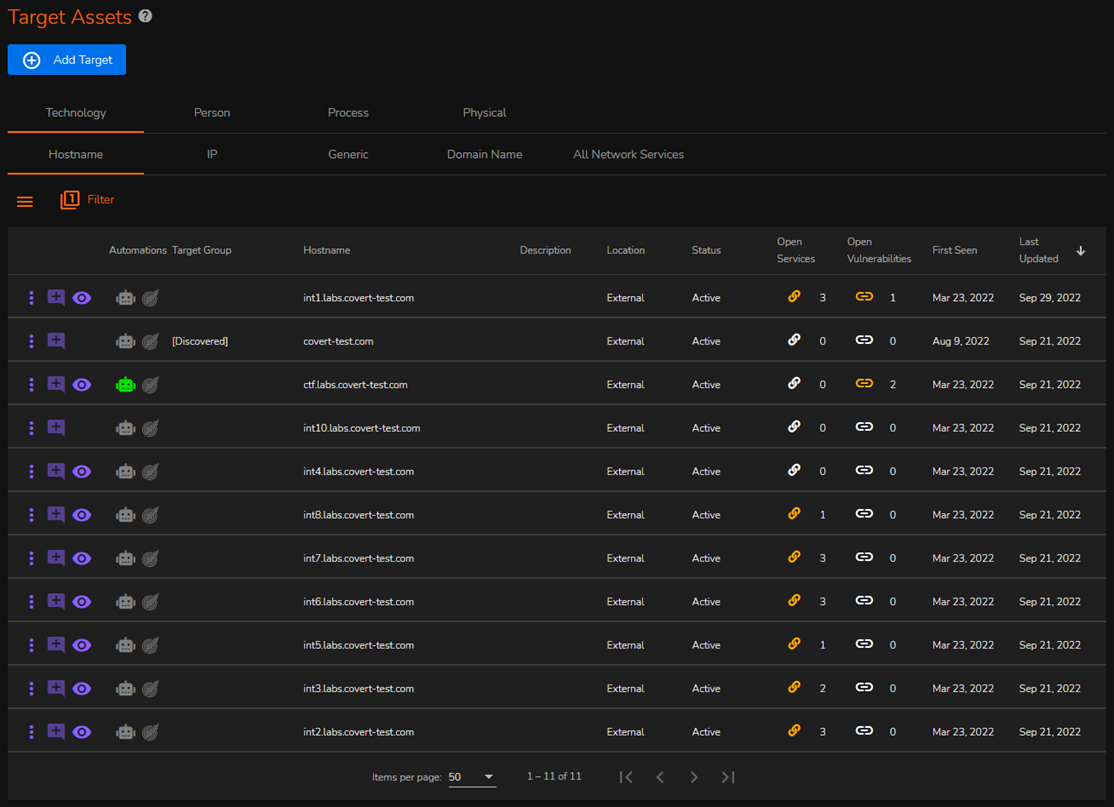
Hostname technology assets view
We believe that this approach allows for granular reporting options (and future extensibility) and a more clear, comprehensive breakdown for you as the reader. This also extends to how we capture vulnerability data, reporting, and much more.
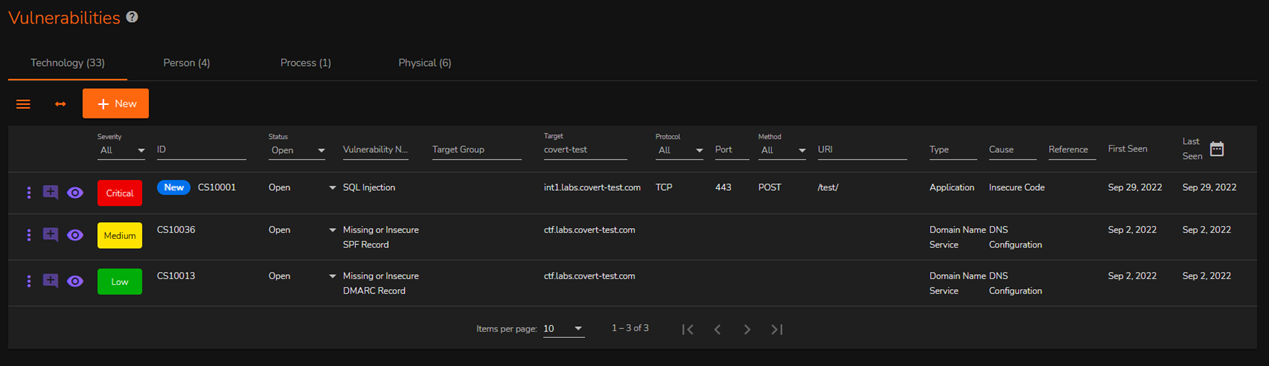
Vulnerabilities view
Whilst we do offer traditional ‘pentest’ reports, which are fully point-in-time and are able to be retrospectively created when needed, the Offensive Operations Centre also serves as a method of visualising the ongoing attack methods and routes to compromise through our Attack Map.

The Attack Map
This is an ever evolving and dynamic way of demonstrating the exercises and activities undertaken by our ‘red team’ as part of our constant cyber-attack mentality here at CovertSwarm. We’ve aligned this with the MITRE ATT&CK tactics and techniques framework, and can tag in specific vulnerabilities, CWEs, and the tools used as each of these breach points (what we like to call ‘nodes’).
As a blue team an engagement, you might only see the occasional alarm go off, a WAF rule being triggered, or an anti-malware alert be raised, and then at the end of the engagement a report will be presented to you with all the issues and other information listed. Our goal with this is to be as covert in our attacks, and as transparent as possible with how we conduct our efforts, and to provide you and your organisation with as much information as possible with every step.
Aside from the day-to-day of our professional services team’s delivery of penetration testing, red teaming, etc., one key element for ourselves is to improve the efficiency (and thus the effectiveness) of how they can operate, which means less of a manual effort towards identifying and reporting upon the ‘noise’ and more upon the target and risk areas that are important to you.
We do this by providing various automations within the OOC, which (at the time of writing) range from the enumeration of technology, people, and physical assets, through to raising vulnerabilities for the ‘noise’ and alerting you to potentially impactful weaknesses. This is one of the downfalls of a traditional penetration testing engagement, wherein you’ll see an enormous list of ‘SSL’ and ‘Certificate’ weaknesses being reported. We still report these (and you can easily filter them out), but unless these types of ‘weaknesses’ can provide a route to compromise we consider them as background noise (they should still be remediated in some form, please do consider that!).
These ‘automations’ aren’t restricted to the team at CovertSwarm, they’re also accessible for all our clients; and whilst they can be run manually through the OOC portal our services are continuously checking for newly created or changed assets, services, and vulnerabilities.
The purpose of this Attack Surface Mapping for our clients and our professional services teams is to be able to identify change – this could be a new service that was exposed to the internet, or a new application endpoint/method, a new physical location for an organisation, or even a newly leaked password that might be successful in a credential-stuffing attack. By automating the detection of change within your organisation:
Another way to look at how our automations can benefit on-going engagements is to acknowledge how much time is spent during one engagement for the trivial-but-arduous task of enumeration and reconnaissance; spending 2-4 hours each engagement to identify possible targets, and then to enumerate them can take a chunk of time for the delivery team. Our automations run continuously and so each and every day the information captured is up-to-date and (importantly) accurate to the current state.
Our development team continue to improve upon our automations, and we have a lot in the pipeline for the next 12 months that the team and I are excited to share in upcoming blog posts like this.
If you would like to enquire about the Offensive Operations Centre please reach out to us via our contact form and our team will get back to you as soon as possible.

Jayson E Street Joins CovertSwarm
The man who accidentally robbed the wrong bank in Beirut is now part of the Swarm. Jayson E Street joins as Swarm Fellow to help us…

iNTERCEPT – How A Small RF Experiment Turned Into A Community SIGINT Platform
I’ve always been fascinated by RF. There’s something about the fact that it’s invisible, the fact that you might be able to hear aircraft passing overhead…

When Your IDE Becomes An Insider: Testing Agentic Dev Tools Against Indirect Prompt Injection
Agentic development tools don’t need to bypass your firewall. They’re already inside. And if an attacker can control what they read, they can control what they…